Table of contents
- Let us start by understanding internet from a common man’s perspective:
- What Does the Internet Mean to You?
- Why is it important for you?
- Now that we understand the major role the internet plays in our lives, let’s take a look at how it actually works.
- What exactly does HTTP do?
- Understanding HTTP :
- Why Is This a Major Problem?
- How HTTP 1.1 Solved the Stateless Problem:
- What is HTTP 2?
- Features of HTTP 2:
- What is TLS?
- Request-Response Model Explained:
- What is the OSI Model?
- The 7 Layers – With Fun Analogies
- How Do These Layers Work Together?
- Why HTTP on the Application Layer?
- Why Does the OSI Model Matter?
- Key Differences between OSI model and Request-Response Model
- What is TCP?
- What is the 3-Way Handshake?
- 3-Way Handshake in HTTP/1.0 vs HTTP/1.1
- Practical Application of TCP (e.g., WhatsApp)
- What is UDP?
- Comparison of TCP and UDP:
- DNS Resolution :
Have you ever wondered how a single click brings the entire world to your screen? Behind the scenes, an intricate network of cables, servers, and protocols works seamlessly to power the internet. This blog takes you on a journey to uncover the fascinating mechanisms that keep us all connected.

Let us start by understanding internet from a common man’s perspective:
What Does the Internet Mean to You?
The internet? It’s a place where I can watch videos, read news, and learn things I didn’t know before. I use it to pay bills, talk to my family, and sometimes even find work. It helps with so many things, but I don’t fully understand how everything happens on it. For me, it’s just something that connects the whole world.
Why is it important for you?
The internet is important because it makes life easier and keeps people connected. For example, with UPI, you can send money in seconds instead of going to the bank. Students can learn online, farmers can check the weather, and small shops can sell things across the country. Without the internet, everything would take more time. Paying bills, booking train tickets, or talking to family far away would be much harder. Life would feel slower and less connected. The internet helps us do things quickly and brings the world closer together. It’s a big part of how we live today.
Now that we understand the major role the internet plays in our lives, let’s take a look at how it actually works.
The internet is a place where people can easily connect with each other using a browser. But what exactly is a browser? A browser is a software application that lets you access and view websites on the internet. For example, when you type a website address like 'google.com' in your browser, it fetches the page for you to see and interact with
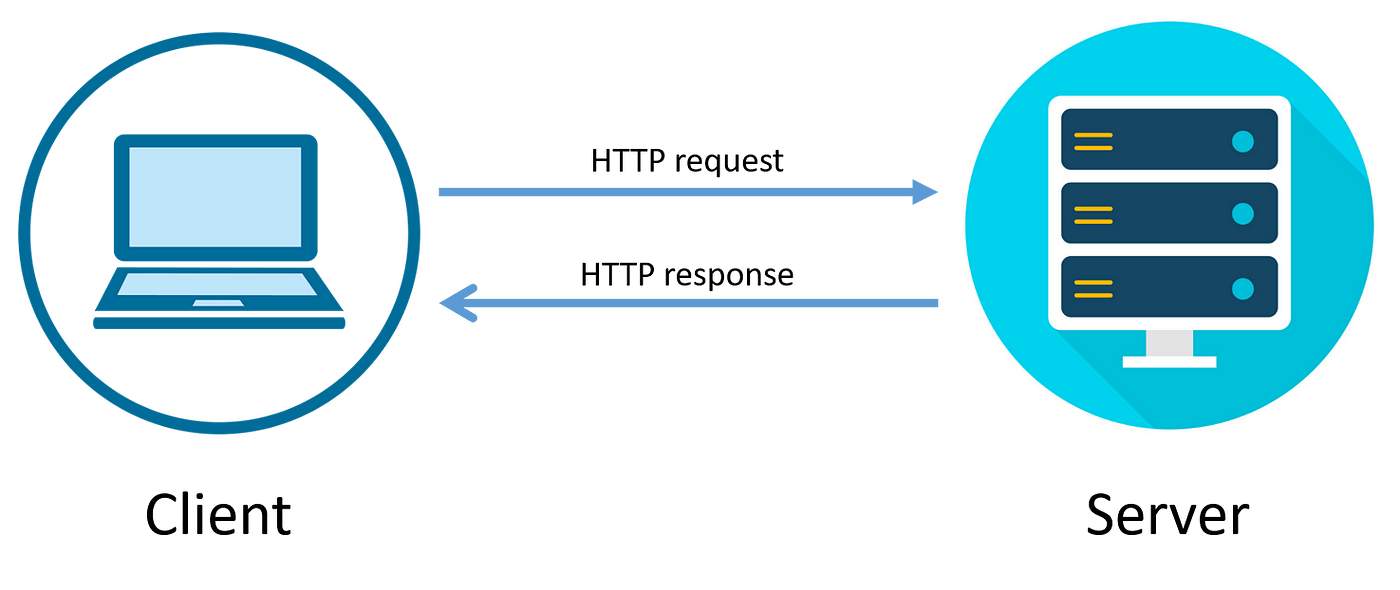
When you search for something on your browser, the information doesn’t just magically appear from your computer. Instead, it’s fetched from servers located somewhere around the world. To get that data, your browser and the server communicate using a set of rules known as protocols. One of the most common protocols is HTTP (HyperText Transfer Protocol).
What exactly does HTTP do?

Think of HTTP as a set of instructions for your browser and the server to talk to each other. Imagine you’re at a restaurant, and you want to order a dish. You tell the waiter what you want, and the waiter takes that request to the kitchen. The kitchen then prepares your order and sends it back to the waiter, who serves it to you. In the same way, when you type a web address, your browser sends a request to the server (like the waiter), the server processes the request (like the kitchen), and sends the response (like the dish) back to your browser. HTTP ensures this whole process happens smoothly every time you visit a website.
Understanding HTTP :
The full form of HTTP is HyperText Transfer Protocol. It was invented by Tim Berners-Lee in 1989 to enable communication between computers over the internet, specifically for sharing information via web pages. HTTP is human-readable, meaning it’s easy for people to understand the data exchanged. However, because HTTP is a stateless protocol, each visit to a website treats the user as new, which creates problems.
Imagine you go to a restaurant and ask the waiter for a glass of water. You drink it, then leave. The next time you visit, you have to ask for the water again, and the waiter doesn't remember that you drank it before. Each time you ask for water, it’s like starting from scratch.
This is what happens in a stateless protocol like HTTP. When you visit a website, the server doesn’t remember you from your previous visit. Each request (like clicking a link or typing a new URL) is treated as if it's your first time. The server doesn’t “remember” anything about you between visits, which can make things slower and less efficient.
Why Is This a Major Problem?
This lack of memory creates issues because it makes browsing inefficient. For example, let’s say you're shopping online:
Without memory: If every page you visit on a shopping website doesn’t remember the items you added to your cart, you’d have to add them again each time you move to a different page. This is frustrating and time-consuming.
With memory: If the website remembers your cart, you can easily continue where you left off. This is the experience you want, but HTTP by default doesn't support it.

How HTTP 1.1 Solved the Stateless Problem:
In HTTP 1.1, persistent connections were introduced. Before this, every time you visited a website, your browser had to ask the server for permission to "talk," and once the information was received, the connection would close. This was like you constantly walking up to a door, knocking, and waiting for someone to answer each time you wanted something. HTTP 1.1 solved this by keeping the door open, so multiple requests could be made without knocking again and again. This saved time and made browsing faster.
What is HTTP 2?
HTTP 2 is the next version of the protocol, which improved HTTP 1.1 by addressing its limitations.
Features of HTTP 2:
Multiplexing:
Imagine you’re sitting at a restaurant, and you order multiple dishes at once. In HTTP 1.1, the waiter would bring one dish at a time, making you wait between each one. HTTP 2 lets the waiter bring all the dishes at once, saving time. Similarly, HTTP 2 allows multiple requests (like images, text, and videos) to be sent at the same time, speeding up webpage loading.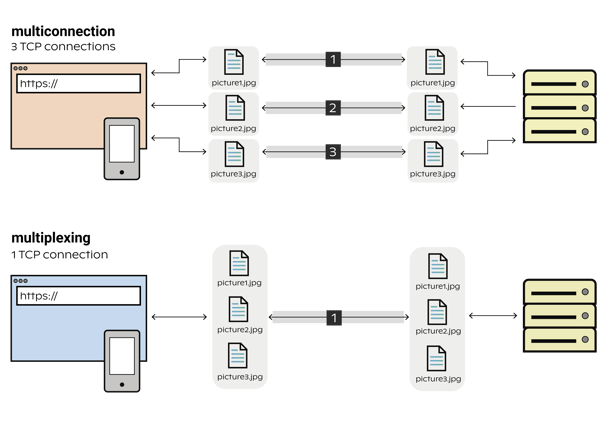
Compression:
Every time you ask for a webpage, your browser sends a request with extra information (called headers). HTTP 2 compresses these headers, which means they take up less space and make the request faster. It’s like packing your clothes in a smaller bag, making it easier and quicker to carry.
Encryption:
Encryption means securing the data being sent so that no one can read it while it’s traveling across the internet. HTTP 2 encourages HTTPS, where the “S” stands for Secure. This uses TLS (Transport Layer Security) to encrypt the connection between your browser and the server, just like locking your mail in a secure envelope before sending it. TLS ensures that even if someone intercepts the data, they won’t be able to read or tamper with it.
What is TLS?
TLS is like a security guard that protects your information while it’s being sent over the internet. It ensures that when you send data (like passwords or credit card details), it stays safe and private. Without TLS, data could easily be intercepted and read by malicious people, just like someone reading a postcard while it’s being delivered.
Fun fact: HTTPS isn't used for internal AWS communication because it adds extra processing for encryption. AWS keeps internal traffic secure using private networks and VPCs, so no need for HTTPS. It’s like locking your room inside a locked house—overkill for extra security!
Now that we know what HTTP is, it's way easier to get the hang of the request-response model. This is basically how your browser chats with a website's server to grab the info you need.
Request-Response Model Explained:

Request:
Think of it like you’re walking into a shop and asking the shopkeeper for something specific, like a product. When you type a website address into your browser, like "example.com", your browser is sending a request to the server that holds that website, asking for the page you want to see. The website’s address, or URL (Uniform Resource Locator), acts like the shop's address, directing the request to the right place.Response:
Once the server receives your request, it processes it and sends back a response. This is the server's way of handing you what you asked for, like the shopkeeper handing you the product. But, the response also comes with a status code—a number that tells you whether the request was successful or not.200 OK: The request was successful, and the server sent back the requested information.
404 Not Found: The server couldn’t find the page you requested. It's like walking into a shop and the item you want is out of stock.
500 Internal Server Error: Something went wrong on the server’s end. It’s like the shopkeeper is too busy or having trouble finding the product.
Example:
Request: You type "example.com" in your browser. Your browser sends a request to the server for that webpage.
Response: The server sends back the webpage, including images and text, along with a status code, like 200 OK, telling your browser everything is good to go.
In simple terms, the request is like you asking the shopkeeper for something, and the response is the shopkeeper handing you what you asked for, with a note to tell you how things went!
Working:
Set up TCP connection:
Your browser (client) sends a request to the server to establish a TCP connection (Transmission Control Protocol). Think of this as your browser knocking on the server’s door, saying "Hi, I’d like to talk!"TLS Certificate Exchange (for HTTPS):
If the connection is secure (HTTPS), the browser and server exchange TLS certificates to ensure the connection is safe. It’s like two people showing their IDs to make sure they’re not impostors before having a secure chat.Send Request:
Your browser sends an HTTP request to the server, including the URL (Uniform Resource Locator), headers (information like browser type, language, etc.), and any data you might be sending (e.g., form submissions). This is like you telling the shopkeeper exactly what you want to buy and how you want it packaged.Get Response:
The server processes the request and sends back a response. This includes the requested data (like a webpage or image), and a status code (like 200 OK or 404 Not Found). The status code tells your browser how the request went—if everything was fine or if there was an issue.TCP Connection Closed:
Once the server sends the response, the TCP connection is closed, like the server saying "I’m done, goodbye!" It’s a polite ending to the conversation, freeing up resources for future requests.
And that’s the entire request-response model in a nutshell!
To help you get a better grasp of the web and the internet, let's break down some important terms using simple analogies that you'll come across frequently!
IP (Internet Protocol):
Like your home address, it helps data find its way to your device. Each device has a unique IP address on the internet.Try yourself activity:You can find the IP address of a website in Linux, you can use the "nslookup" or "dig” command in the terminal, followed by the website domain name; for example, to find the IP address of "google.com", type "nslookup google.com" or “dig google.com” in the terminal.
URL (Uniform Resource Locator):
Think of it as a street address for a house. It tells your browser exactly where to find a website.
DNS (Domain Name System):
It’s like a phone book that translates a URL (like "www.example.com") into an IP address (like "192.168.1.1"), helping your browser find the server.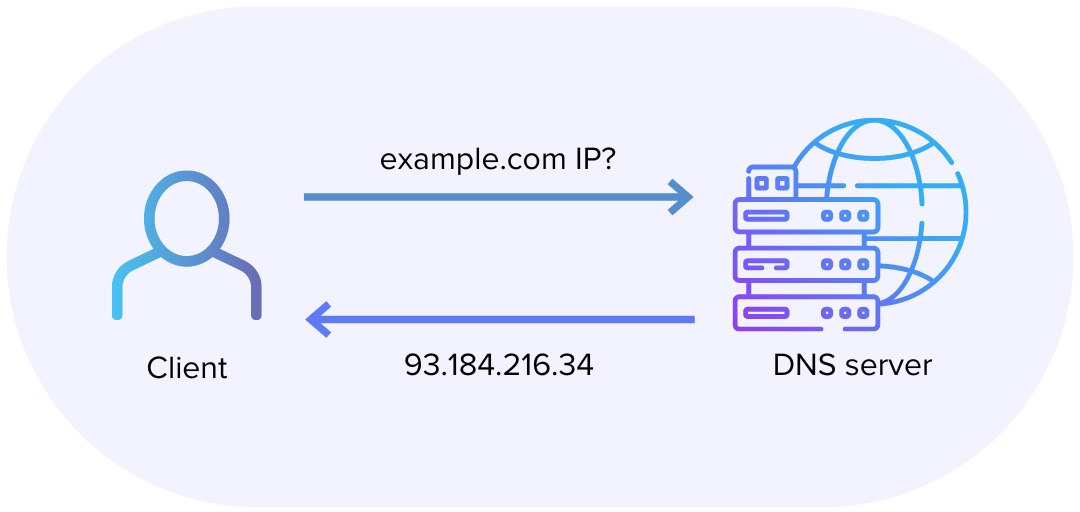
Header:
Like the envelope of a letter, it contains information such as the sender, recipient, and details on how the data should be handled.Payload:
The actual message inside the envelope, such as the webpage content, images, or data you’re sending.Cache:
Think of it as your memory. Your browser stores parts of websites (like images or text) so they load faster the next time you visit.Protocol:
This is like a set of rules for communication. HTTP is the protocol that tells your browser and the server how to talk to each other.Cookie:
You’ve probably noticed those pop-ups when you visit a website for the first time, asking you to accept cookies. Cookies are like a small note that a website leaves in your browser to remember things about you, like your login info or preferences.
SSL/TLS (Secure Socket Layer / Transport Layer Security):
Like a secure envelope for sending your personal data, it keeps information safe when you use HTTPS on websites. It ensures that no one can read or tamper with your data while it’s being sent.Bandwidth:
Think of it like the width of a highway. More bandwidth means more data can travel at once, leading to faster internet speeds.
Alright, now that you’ve got a hang of the basic buzzwords and understand how browsers and servers talk to each other, let’s dive into the OSI Model! 🕵️♂️ Think of it like peeling back the layers of an onion (or a cake if you're hungry). It’s all about breaking down how data moves across a network, one step at a time.
Ready? Let’s unravel this 7-layer masterpiece. 🎂
What is the OSI Model?
The OSI (Open Systems Interconnection) Model is like a recipe for network communication. It splits the journey of data into 7 layers, each with a unique job. Every layer is like a step in sending a message—from typing a WhatsApp text to seeing "Message Delivered" on your friend's phone.
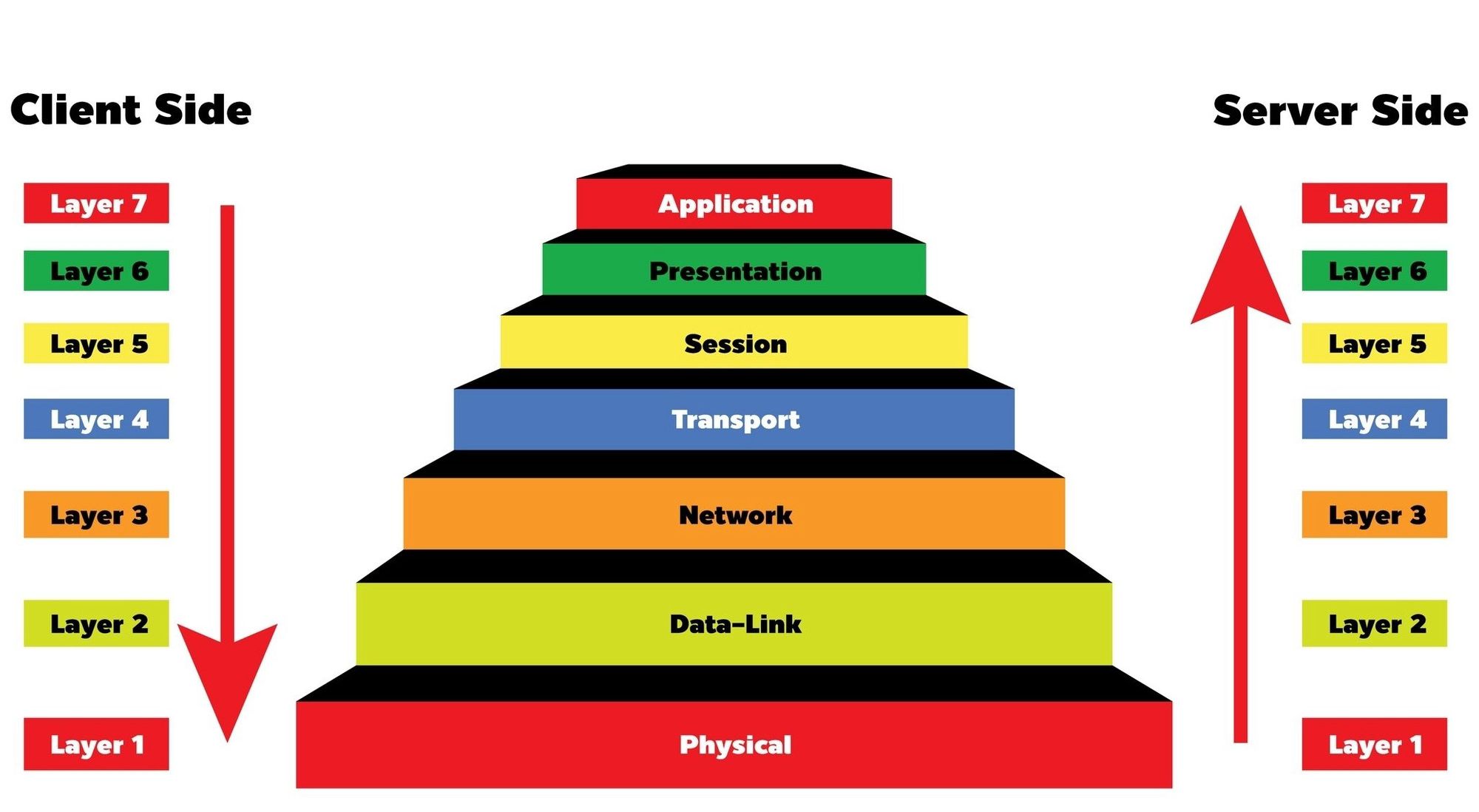
The 7 Layers – With Fun Analogies
Physical Layer – The Courier's Wheels 🚗
What it does: Moves raw bits (1s and 0s) as signals (electric, light, or radio) across wires or airwaves.
Analogy: Imagine a courier’s wheels rolling on the road, carrying your package. No wheels, no delivery!
Example: Cables, Wi-Fi signals, or fiber optics.
Data Link Layer – The Packing Team 📦
What it does: Packs raw data into nice, labeled packages (called frames) and ensures no mix-ups in local delivery.
Analogy: This is like workers boxing up goods and slapping on labels to say, "Send this box to Warehouse B."
Example: MAC addresses (like a device's unique shipping ID).
Network Layer – The GPS Navigator 🗺️
What it does: Finds the best route to send your data to its final destination.
Analogy: The truck driver uses GPS to figure out how to get from City A to City B.
Example: IP addresses (your device’s "address"), routers.
Transport Layer – The Delivery Manager 📋
What it does: Breaks your message into chunks (segments) and ensures every chunk gets delivered safely and in the correct order.
Analogy: If any box falls off the truck, the manager ensures it’s sent again. No missing pieces!
Example: TCP (careful delivery) or UDP (fast but no guarantees).
Session Layer – The Gatekeeper 🚪
What it does: Manages the connection between sender and receiver, keeping it open until the job’s done.
Analogy: Like a bouncer at the door who only lets your delivery person talk to the recipient.
Example: When you stay logged in to a website.
Presentation Layer – The Translator 📖
What it does: Converts data into something both sender and receiver can understand. Also handles encryption.
Analogy: Imagine translating labels on the package into the recipient's language or locking it in a safe to prevent theft.
Example: Data compression, encryption (e.g., HTTPS).
Application Layer – The Front Desk 🛎️
What it does: This is the final stop where the user interacts with the data.
Analogy: The front desk clerk hands over the package and says, “Here’s your order!”
Example: Web browsers (HTTP), email apps (SMTP), and file transfer tools (FTP).
How Do These Layers Work Together?
Think of data traveling down the layers when sent and climbing back up when received:
You (the user) request a YouTube video (Application Layer).
It gets encrypted and formatted (Presentation Layer).
A session is set up between you and YouTube (Session Layer).
The video is broken into smaller pieces (Transport Layer).
Each piece gets a route to YouTube (Network Layer).
It’s packed into frames for local transmission (Data Link Layer).
Finally, it’s sent as raw signals over Wi-Fi or cables (Physical Layer).
Once YouTube’s server gets the request, it reverses the process to deliver your video.
HTTP (HyperText Transfer Protocol) works on the Application Layer, which is the topmost layer in the OSI Model.
Why HTTP on the Application Layer?
The Application Layer is responsible for providing network services to end-user applications like web browsers, email clients, or file-sharing tools. HTTP is a protocol specifically designed to enable communication between a client (e.g., your browser) and a web server, allowing them to exchange HTML, CSS, JavaScript, images, and more.
Why Does the OSI Model Matter?
Troubleshooting Made Easy: If something’s broken, you know which layer to check. For example:
Can’t connect to Wi-Fi? Check the Physical and Data Link Layers.
Page not loading? The issue could be in the Network or Transport Layer.
Interoperability: All these layers mean devices and apps can work together even if they’re from different vendors.
Key Differences between OSI model and Request-Response Model
| Aspect | OSI Model | Request-Response Model |
| Purpose | Describes the structure of network communications across seven layers. | Defines a pattern for interaction between a client and a server. |
| Scope | Covers end-to-end communication across the network stack. | Focused on specific interactions, typically in the application layer. |
| Abstraction Level | Conceptual framework for networking. | Practical implementation pattern in systems/applications. |
| Applicability | Used to design, understand, and troubleshoot networks. | Used in software, APIs, and web-based client-server communication. |
| Layers | Involves seven distinct layers, each with its own role. | Involves two parties: client and server. |
Data can be transferred between machines in two main ways: TCP and UDP.
What is TCP?
TCP (Transmission Control Protocol) is a reliable communication protocol that ensures data is transferred accurately and in the correct order between devices. Here's what makes TCP special:
No data is lost during transmission. Every packet sent by the client is guaranteed to reach the server.
Ordered: Data packets arrive at the destination in the same sequence in which they were sent.
It takes more time compared to UDP but is reliable.
TCP establishes a stable connection between devices using a 3-way handshake.This synchronization process ensures that both the sender and receiver are ready to exchange data.
What is the 3-Way Handshake?

The 3-way handshake is the process TCP uses to establish a connection between two devices before they start exchanging data.
Analogy:
Imagine two people meeting to start a conversation:
Person A waves and says, "Hi, can we talk?" (This is the SYN message from the client.)
Person B waves back and says, "Sure, let's talk." (This is the SYN-ACK message from the server.)
Person A nods and says, "Great, let's begin!" (This is the ACK message from the client.)
Now that the handshake is complete, the two can start their conversation (data transfer). This process is a cornerstone of TCP’s stability and reliability.
3-Way Handshake in HTTP/1.0 vs HTTP/1.1
In HTTP/1.0, the 3-way handshake (TCP connection setup) had to be performed every time a client made a new request to the server. This meant that for every file (HTML, CSS, JavaScript, images) needed to load a webpage, a new connection was established, resulting in significant overhead and slower performance.
With HTTP/1.1, a feature called persistent connections was introduced. The 3-way handshake is performed only during the initial connection setup, and the same connection is reused for multiple requests and responses between the client and server. This eliminates the need to repeatedly establish new connections, reducing latency and improving efficiency, especially for web pages with multiple assets.
Practical Application of TCP (e.g., WhatsApp)
TCP is ideal for reliable communication, such as WhatsApp messaging, where every packet of data (text or media) must reach its destination without loss. TCP ensures messages are delivered accurately and in the correct order, using retransmissions for any lost data and acknowledgments for delivery status. For example, when you send a message, TCP guarantees its successful delivery, enabling features like "double ticks" for confirmation.
Why TCP is Not Used for Video Calling (e.g., Zoom)
TCP is unsuitable for video calling because it prioritizes reliability over speed, leading to delays. It retransmits lost packets, causing high latency, which disrupts the real-time nature of calls. In contrast, missing a few frames or words is acceptable in video calls, where timing is more critical than perfect accuracy.

This makes UDP a better alternative for such scenarios, as it offers lower latency by skipping retransmissions.
What is UDP?
UDP (User Datagram Protocol) is a fast and lightweight communication protocol used in networking. Unlike TCP, it does not establish a connection before transmitting data, which makes it ideal for applications where speed and low latency are more important than reliability. UDP is often used in real-time applications like video streaming, gaming, and voice calls, where quick delivery is preferred even if some data is lost.
Key Features of UDP
Minimal Latency:
- UDP has less overhead compared to TCP, which means the time taken to send data is lower. This results in minimal latency, making it suitable for real-time applications where speed is critical.
Less Reliable:
- UDP does not guarantee that all packets will be delivered. If packets are lost during transmission, they are not retransmitted.
No Acknowledgment or Ordering:
- UDP does not acknowledge packet receipt or ensure packets are received in order, which means not all packets sent will be received by the receiver.
Connectionless:
- UDP is a connectionless protocol, meaning it doesn’t require the establishment of a connection between sender and receiver before sending data.
Applications of UDP

Live Video and Voice Calls (e.g., Zoom, WhatsApp calls)
Online Gaming (e.g., real-time games)
Live Streaming (e.g., YouTube, Twitch)
DNS Queries and DHCP Requests
Why Use UDP?
UDP is preferred in scenarios where speed and real-time performance are more important than ensuring that every single packet is delivered. This makes it ideal for applications that can tolerate some loss of data but need to operate without delay.
Comparison of TCP and UDP:

| Feature | TCP (e.g., WhatsApp) | UDP (e.g., Zoom) |
| Reliability | Guarantees no data loss | Allows data loss for speed |
| Order Guarantee | Ensures packets are in order | Packets may arrive out of order |
| Latency | High, due to retransmissions | Low, prioritizes real-time data |
| Use Case | Messaging, file transfer, email | Video calls, online gaming |
Now that we understand how data is transmitted from the user to the server, let's explore how a computer locates the IP address of a URL using DNS. DNS (Domain Name System) is responsible for converting a human-readable domain name (such as www.example.com) into an IP address that computers can use to communicate with each other over the network. Here's how the process works:
DNS Resolution :

DNS Query is initiated when the user types a domain name into the browser.
Local Cache is checked first for the IP address.
If not found, the DNS Resolver (ISP server) is queried.
The Resolver asks the Root DNS Server.
The Root Server directs the query to the TLD DNS Servers.
The TLD Server points to the Authoritative DNS Server for the domain.
The Authoritative Server responds with the IP address.
The Resolver returns the IP address to the user’s browser.
The Browser uses the IP to establish a connection and retrieve the requested resource.
There are 13 root servers located at various parts of the world

By utilizing DNS, systems can use human-readable names rather than having to remember numeric IP addresses, which makes the internet more user-friendly.
Since DNS queries typically involve small amounts of data and require fast response times, DNS operates over the UDP protocol on port 53. The lightweight nature of UDP allows for quick transmission without the need to establish a connection, making it ideal for the small and time-sensitive nature of DNS queries.
So, through this article, we've learned that understanding the basics of networking is super important for web development. Knowing how DNS resolution works, how data travels using protocols like HTTP/HTTPS, and the client-server model helps developers handle web interactions smoothly. Plus, being familiar with IP addressing, ports, and hosting environments is key to boosting performance, security, and scalability, which is essential for creating efficient and reliable web applications. This foundational networking knowledge is crucial for building strong, responsive, and secure web apps. Thank you for reading my blog, also do consider following me on LinkedIn!
LinkedIn: www.linkedin.com/in/vishaltantri22
